Social Engineering
The Art of the seemingly impossible
Do you think Cyber criminals just use complicated software to hack into your system?WRONG!
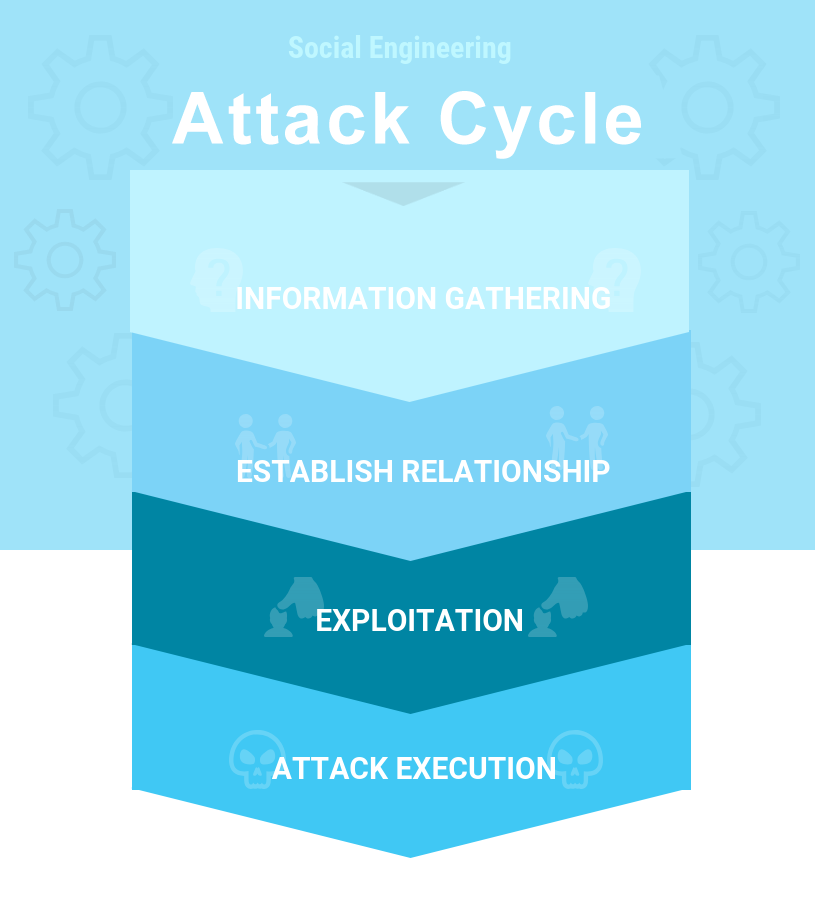
Human Hackers use an Attack Cycle to deceive and manipulate your employees into divulging information to be used to hack into your systems.
This includes methods such as:- A panic phone call to I.T. department to reset a password.
- Face 2 Face posing as a support I.T. worker to gain entry into the main server room.
- An email pretending to be from Human Resources & then gathers personal information.
- A phising email or text promising something in return eg confirm log in details and bank account details to ensure salary is paid on time.
Cyber Training - Classroom - Webinar - eLearning
Often described as highly engaging and ‘fun’ our 1-day classroom or webinar learning sessions, includes a structured role-play exercise and a review of the learning points delivered in the course. In doing so we not only educate the attendees but also empower them as a vital part of your organisation’s defence against cyber-crime. IHF Cyber Security Human Factors Certification will be awarded on full attendance of the course.
Get in touch today
One of our human factors associates will be on hand to learn about your business and see if we can help.



